Rapidly detect and respond to zero day vulnerabilities impacting your third-party ecosystem. Minimize risk, maximize efficiency with Bitsight Vulnerability Detection & Response. Your proactive shield in critical moments.
Rapidly detect and respond to zero day vulnerabilities impacting your third-party ecosystem. Minimize risk, maximize efficiency with Bitsight Vulnerability Detection & Response. Your proactive shield in critical moments.
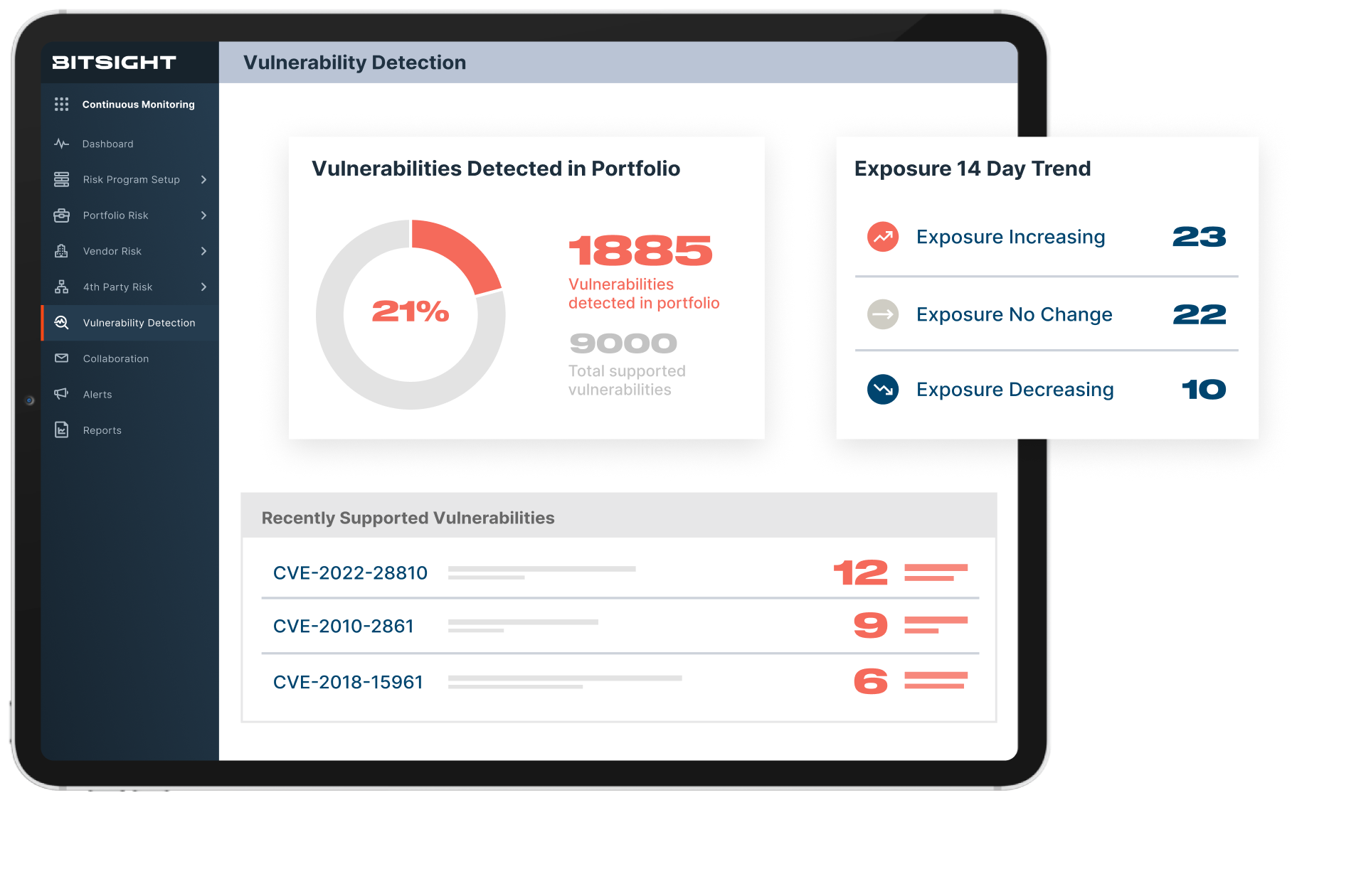
Cut through the chaos of zero days
Cut through the chaos of zero days
Tired of the fire drills during zero days? Say goodbye to the confusion, endless emails, and spreadsheet headaches. Bitsight simplifies vendor prioritization, outreach, and tracking—giving you clarity and peace of mind when it matters most.
Master Zero-Day Defense: Speed, Precision, and Compliance
Stay ahead of the game with market-leading vulnerability intelligence. Detect, manage, and mitigate zero-day events swiftly. Effortlessly scale and track vendor outreach with precision. And close security gaps faster than ever to confidently meet regulatory requirements.
We can now easily identify the vulnerabilities associated with a particular vendor and how those vulnerabilities could impact our own security posture—before we begin working with them.”
Spot vendor exposure—and take action.
Prioritize Vendor Exposure
Shine a light on critical risk
Prioritize Vendor Exposure
Shine a light on critical risk
Gain easy access to critical vulnerability exposure in your third-party ecosystem. Quickly sort exposure by severity and impact—and address risk where it matters.
Share external evidence
Pinpoint exposure to vendors
Share external evidence
Pinpoint exposure to vendors
Accelerate zero day remediation with evidence of vulnerable vendor assets and versions. Connect the dots to protect their organization— and yours.
Scale Questionnaire Outreach
Bulk outreach to impacted vendors
Scale Questionnaire Outreach
Bulk outreach to impacted vendors
Alert impacted vendors with a couple clicks to speed up the outreach and remediation process. Leverage bulk questionnaire sends—tailored with exposure evidence—to move quickly when the clock is ticking.
Track Progress
Stay compliant while reporting to stakeholders
Track Progress
Stay compliant while reporting to stakeholders
Communicate outreach and remediation progress in real time with concise reporting on vendor questionnaire responses. Inform your business to address potential exposure.
Bitsight Managed Services for Third-Party Risk Management

Bitsight Managed Services for Third-Party Risk Management
Don't let limited resources hold you back. Break free from reactiveness with managed services to run your entire third-party risk program—and shift your focus to growing your business.
Explore Vulnerability Detection & Response
Resources
Bitsight Third-Party Vulnerability Detection & Response

Bitsight Third-Party Vulnerability Detection & Response
Bitsight Continuous Monitoring

Bitsight Continuous Monitoring
Webinar: Responding to Zero Days at Scale

